React2Shell (CVE‑2025‑55182): Critical Vulnerability in React Server Components

“There is an unauthenticated remote code execution vulnerability in React Server Components. We recommend upgrading immediately.” - Source: React blog post.
A critical flaw in React Server Components (RSC) turned into a live-fire event within hours. Public PoCs appeared, cloud providers reported probing at scale, and frameworks rushed patches. If you run React 19 or frameworks that implement RSC (notably Next.js App Router), this is a “upgrade first, investigate next” moment.
Why is this important?
React2Shell is unauthenticated remote code execution in a mainstream web stack, many internet‑facing apps are reachable by default and public exploits lower the bar for attackers.
A successful hit lets an adversary run code on your servers, harvest secrets (database credentials, API keys, cloud tokens), and pivot into your cloud or data. CISA added CVE‑2025‑55182 to the Know Exploited Vulnerabilites (KEV) catalog on December 5, 2025, confirming in-the-wild exploitation and setting a remediation deadline.
AWS reports rapid, multi‑actor attempts - including China‑nexus groups - and details hands‑on‑keyboard behavior refining payloads against real targets. - Source: AWS Security blog post.
The right response is fast, targeted reduction: patch the affected services first, rotate sensitive secrets, and validate closure.
What is React2Shell, exactly?
React2Shell (CVE‑2025‑55182) is an unauthenticated RCE caused by unsafe deserialization in RSC's payload decoding for server function endpoints (CWE‑502).
- Affected upstream packages are react‑server‑dom‑webpack, react‑server‑dom‑parcel, and react‑server‑dom‑turbopack in React 19.0.0, 19.1.0, 19.1.1, and 19.2.0. 🩹 Fixes landed in 19.0.1, 19.1.2, and 19.2.1 - Source: React blog post.
- Downstream, Next.js App Router is affected across 15.x and 16.x, plus canaries after 14.3.0‑canary.76. 🩹 Patched releases include 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, and 16.0.7, with patched canaries available.
ℹ️ Note: Next.js issued an advisory and dedicated CVE entry (CVE-2025-66478) to track the downstream impact of React2Shell.
Two critical nuances from the React team:
- Apps may be vulnerable even if you don’t explicitly use server functions ➡️ if they support RSC, they need to be updated.
- Coordinated mitigations are in place at hosting providers, but you should not rely on them instead of patching.
What is the timeline?
The timeline highlights how quickly this escalated from disclosure to active exploitation:
- Dec 03: NVD publication and upstream advisory; first public PoCs observed.
- Dec 03: First weaponized exploit appears (beyond simple PoC).
- Dec 04: First named threat actor reported engaging the CVE.
- Dec 05: CISA adds CVE‑2025‑55182 to the KEV catalog (in‑the‑wild exploitation confirmed).
- Dec 05+: Additional exploit variants surface; continued probing across cloud workloads.
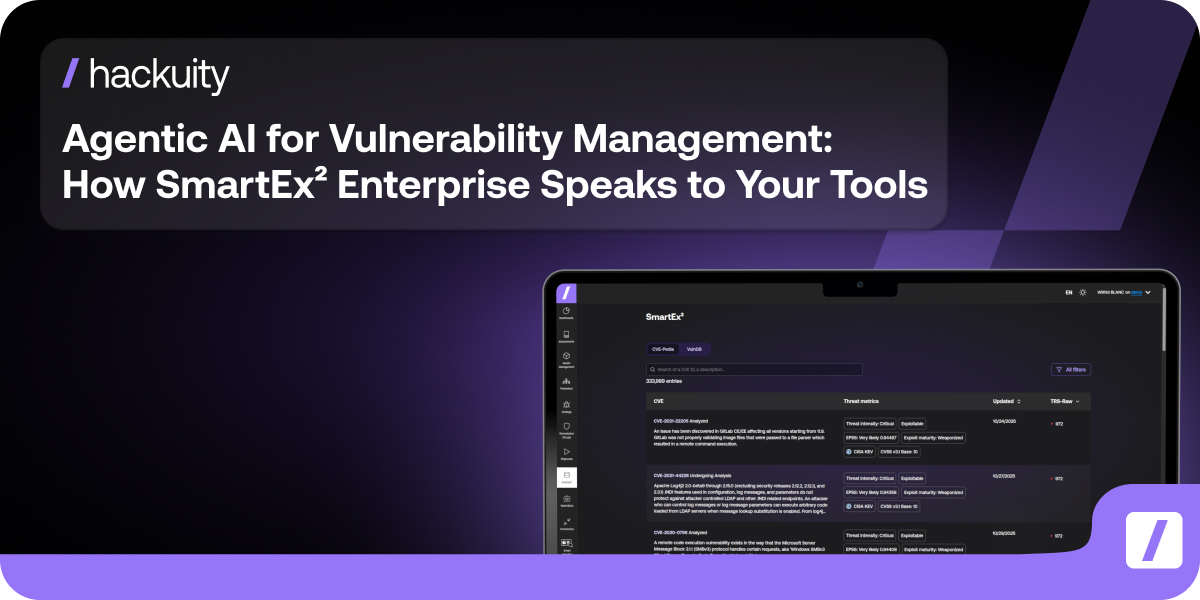
Source: Hackuity - SmartEx² Entreprise module
What to do right now: Patch or Perish!
- Upgrade React and Next.js to fixed versions per upstream guidance. There is no reliable workaround.
- Don’t rely on WAF alone. Providers have shipped rules, but they can’t guarantee coverage against evolving variants.
- If you were online and unpatched after public PoCs, rotate secrets and review logs for suspicious POSTs to server action endpoints, reverse shells, and unexpected process spawns.
- Patched versions for Next.js:15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, and 16.0.7; patched canaries 15.6.0‑canary.58 and 16.1.0‑canary.12. If on Next.js 14.3.0‑canary.77+ canaries, downgrade to the latest stable 14.x.
Why this matters for CTEM
React2Shell is a landmark vulnerability that demonstrates how quickly a modern software ecosystem can expose thousands of organizations to immediate risk. The combination of:
- a framework-level flaw,
- trivial exploitation,
- widespread usage,
- and near-instant weaponizationcreates a perfect storm for defenders.
This incident is a powerful reminder that exposure management is no longer optional.
Organizations must be able to dynamically inventory their technologies, measure exposure, prioritize remediation, and react at the pace of attackers.
If you want to see the current SmartEx² Enterprise view for CVE‑2025‑55182 and how to launch a focused remediation campaign in your organization, request a short demo below, and we’ll walk you through it 👇
What is React2Shell, exactly?