CVSS Is Necessary, But Not Sufficient. Here's Why.


You've got a “Critical” CVSS score. Now what?
In the article about CVSSv4 adoption, we saw that CVSS gives you a number. That number tells you the vulnerability is severe. It doesn't tell you whether attackers are actively exploiting it. It doesn't tell you if it's on an internet-facing server or an isolated dev box. It doesn't tell you if you have detection coverage or strong compensating controls.
That gap between severity and risk is where security teams get stuck. CVSS v4 brought improvements to severity scoring, with adoption accelerating faster than expected and more accurate base scores. But even with those improvements, CVSS wasn't designed to answer the operational question: what do I fix first?
That's the problem Hackuity's True Risk Score (TRS) solves.
What CVSS Does (And Doesn't Do)
CVSS provides standardized severity measurement. It's essential. Hackuity fully supports both CVSS v3.1 and v4.0 because that baseline matters.
But CVSS was never meant to be your prioritization engine. Even with recent improvements, it has boundaries:
Threat intelligence is limited. CVSS includes some threat metrics as supplemental data. But it doesn't capture whether there's active exploitation in the wild, whether exploit kits are circulating, or what the probability of exploitation looks like over the next 30 days.
Environmental context is incomplete. CVSS Environmental metrics let you adjust for CIA requirements. But they don't tell you whether the impacted Asset is internet-facing, how well it's protected, whether you have detection coverage, or how widely the vulnerable component is deployed.
CVSS measures severity. You need risk.
How TRS Bridges the Gap
TRS takes CVSS as its foundation and adds two critical dimensions: real-world threat intelligence and your actual environment.
.png)
The Threat Intelligence Layer
TRS pulls from four distinct threat intelligence factors to build a complete threat picture:
Exploitability tracks whether working exploit code exists, from proof-of-concept through weaponized frameworks.
Exploit Maturity assesses how accessible exploitation is.
Threat Intensity measures current attacker interest based on observed campaigns and targeting patterns.
EPSS integration adds probabilistic prediction using the industry-standard Exploit Prediction Scoring System.
A CVSS 9.8 with no known exploits gets a different TRS than a CVSS 7.5 with active exploitation. That distinction matters when you're deciding what to patch this week.
The Environmental Context Layer
TRS captures how your infrastructure and security posture affect risk:
Asset Criticality incorporates CIA requirements for each asset. Systems handling sensitive data get appropriately weighted.
Asset Exposure distinguishes internet-facing systems from internal networks or air-gapped environments.
Protection Measures account for segmentation, firewalls, endpoint protection, and hardening. Strong protections reduce risk.
Detection Measures consider your monitoring coverage and response capabilities.
Distribution captures how widely deployed the vulnerable component is.
This is the difference between theoretical severity and actual risk in your environment.
A Simple Example
Here's the concept in action:
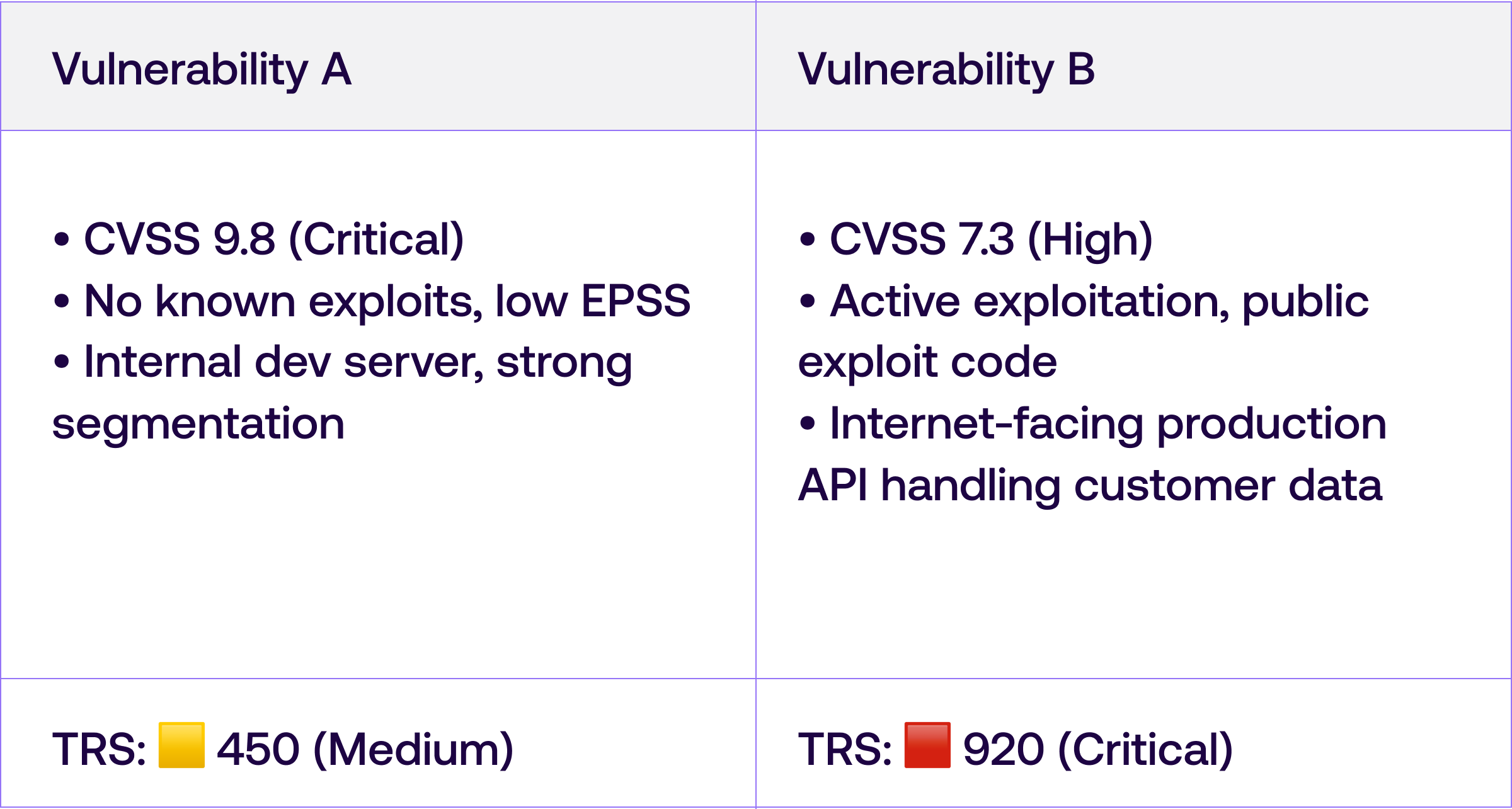
Traditional CVSS-only prioritization says fix A first. TRS makes the right call obvious: B is your urgent priority.
What This Looks Like in Practice
When you apply TRS across an entire vulnerability portfolio, the distribution shifts dramatically:
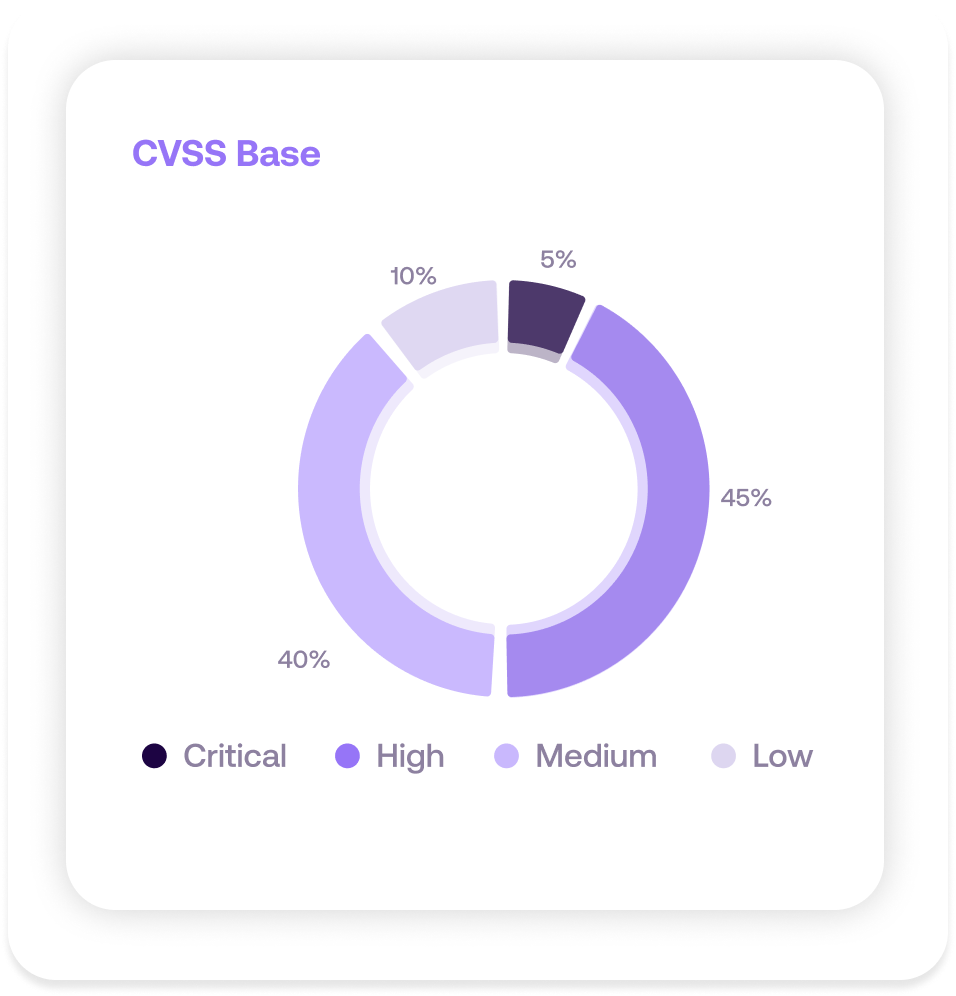
Typical customer environment showing distribution by CVSS Base score
CVSS Base scores cluster at the top. Which ones do you fix first? The score alone can't tell you.
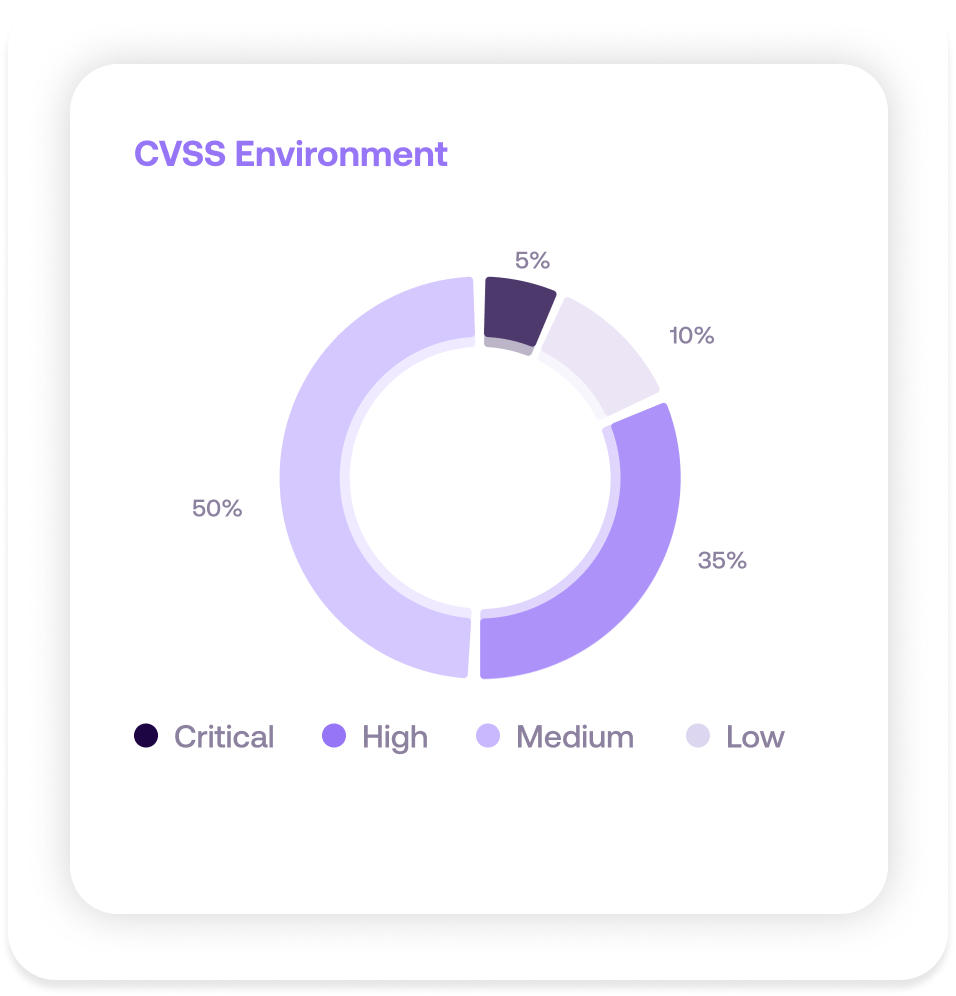
Same environment with CVSS Environmental scores applied.
As expected, we see that the addition of Temporal and Environmental metrics on top of the CVSS Base metrics helps reducing the volume of “Critical” and “High” Findings, passing from 50% with CVSS base only to 40% in CVSS Environmental. You still face too many "Critical" and “High” Findings with no clear differentiation.
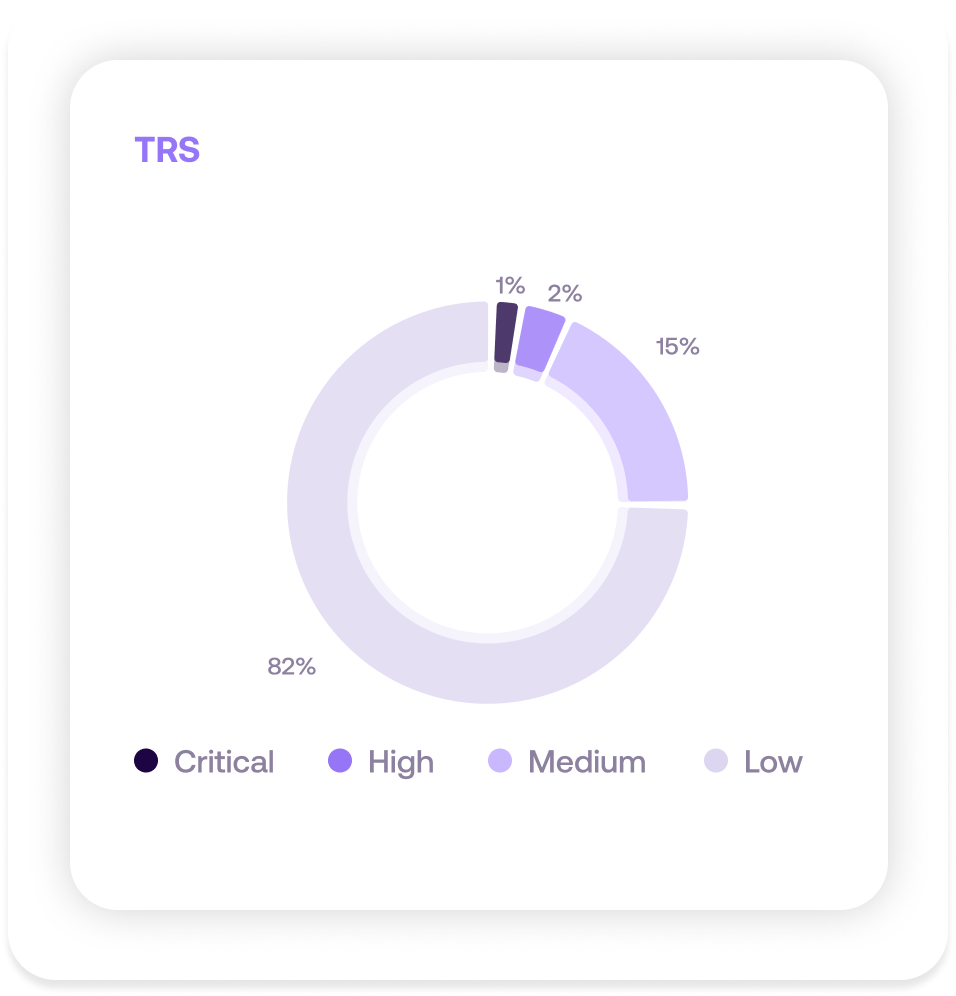
Same environment scored with TRS
TRS changes the picture entirely. “Critical” and “High” Findings drop to a manageable number (from 40% in CVSS Environmental to 3% in TRS), because those labels are reserved for vulnerabilities that meet three conditions: high or critical technical severity, real exploitation threat, and meaningful exposure in your environment.
The “Medium” and “Low” severities expand to hold findings that, while technically severe, don't pose immediate risk given your specific context. This isn't hiding problems. It's providing the clarity you need to act effectively.
The "Zero Critical TRS" Target
This distribution shift makes an ambitious goal achievable. Many of Hackuity's enterprise customers set a simple target: zero Critical TRS findings. And they achieve it.
Why does this work when "zero Critical CVSS" often doesn't?
Because “Critical” in TRS is rare and defensible. It's the intersection of substantial technical impact, real exploitation or high near-term likelihood, and meaningful exposure in your environment.
When something hits “Critical” TRS, your team knows it's genuinely urgent. Security teams know where to focus. Engineering teams understand why it matters. Management sees measurable progress.
From Severity to Risk
CVSS provides the language for describing vulnerability severity. TRS makes it operational.
It fuses CVSS scoring with real-time threat intelligence and your specific environment to answer the question that CVSS alone can't: what should I fix first, given my actual risk?
Vulnerability management needs both: accurate severity measurement and contextual risk assessment. CVSS handles the first. TRS delivers the second.
If you want to see how TRS transforms your vulnerability prioritization, request a demo below. We'll walk you through how it works with your actual findings.👇



