CVSS v4, Two Years On: What The Data Really Says


When CVSS v4 launched in November 2023, the security community had questions.
Would organizations actually adopt it? Would the refined scoring methodology deliver on its promises? And most importantly, would it help security teams make better decisions?
Two years in, we finally have answers. And they're not what everyone expected.
The Adoption Story: Faster Than You'd Think
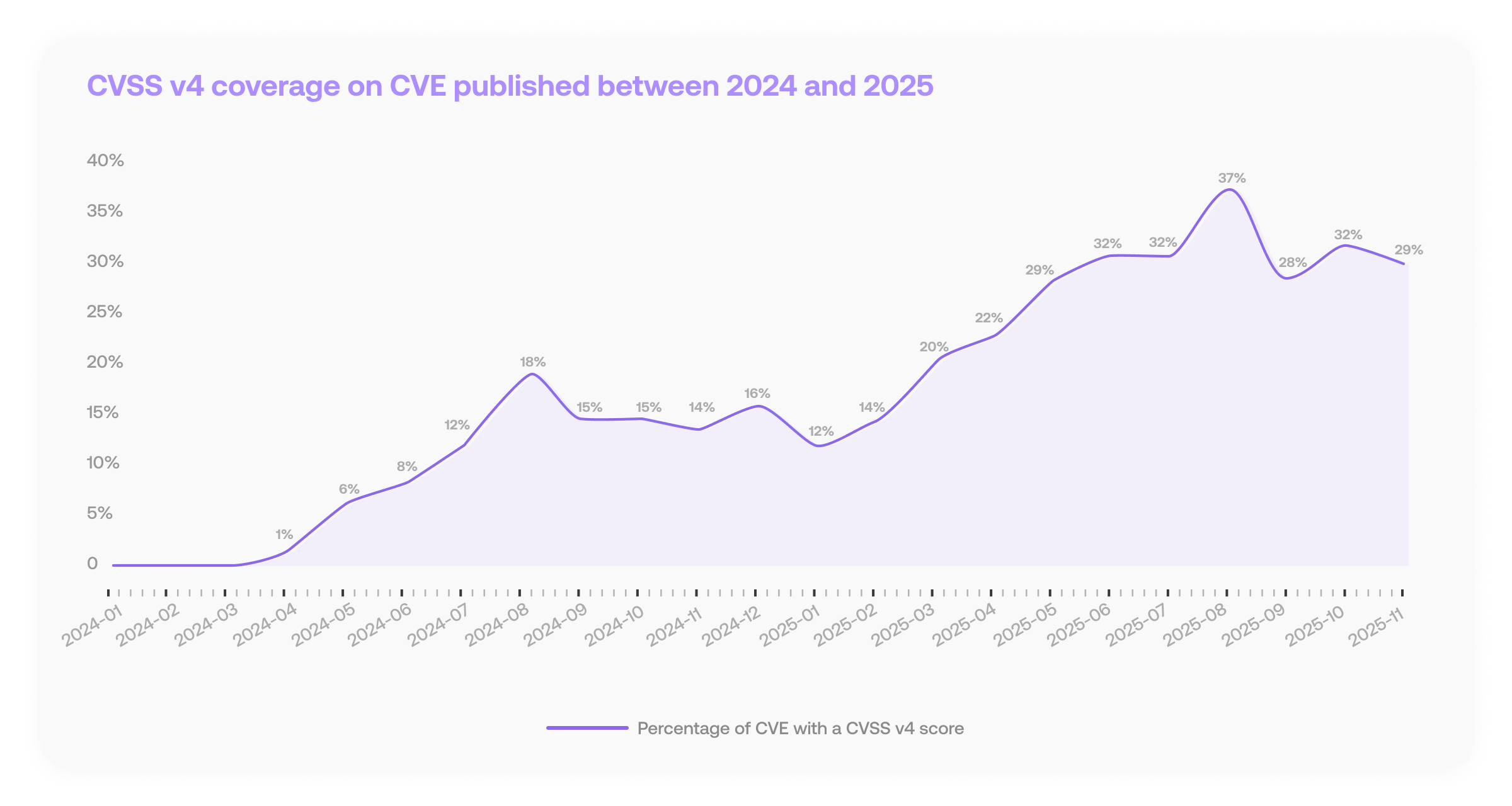
Let's start with the big picture. In 2023, CVSS v4 adoption was basically nonexistent. But by mid-2024, something shifted. The numbers tell a clear story:
- 2024: 8.88% of newly scored CVEs got CVSS v4 ratings
- 2025: That jumped to 25.49%, nearly triple the previous year
- Peak month (August 2025): 36.88% of CVEs received v4 scores
This is faster adoption than many people predicted. Nearly all scored CVEs still have CVSS v3 scores (99.3%), but the momentum behind v4 is unmistakable. Over 14,000 CVEs have been scored with v4, and 84.7% of those also carry v3 scores.
The Score Shift: Lower, But More Accurate
Here's where it gets interesting. When you compare v3 and v4 scores for the same vulnerabilities, v4 scores trend lower. On average, 1.1 points lower.
What's driving this change?
Looking at 11,881 CVEs scored in both versions:
- 52% received lower v4 scores (6,173 CVEs)
- 25.6% stayed roughly the same (±0.5 points)
- 22.4% actually got higher v4 scores (2,662 CVEs)
The lowering isn't random. It's targeted. The vulnerabilities getting downgraded the most? SQL injection and RCE vulnerabilities that, under v3, may have been overscored.
Vulnerability types with the biggest downgrades:
- Pre-Auth SQL Injection: -2.8 points average (1,567 CVEs)
- Post-Auth SQL Injection: -2.4 points average (745 CVEs)
- Pre-Auth RCE (Command/Code Injection): -2.4 points average (273 CVEs)
This isn't score inflation in reverse. It's recalibration. CVSS v4's refined methodology accounts for Attack Requirements and more granular User Interaction, giving a clearer picture of what it actually takes to exploit a vulnerability.
Severity Reclassification: The Numbers Are Eye-Opening
When you look at severity category shifts, the changes become even more obvious.
The most common severity changes:
- 2,427 CVEs dropped from Critical to Medium
- 1,917 CVEs fell from High to Medium
- 453 CVEs rose from Medium to High
That's over 4,300 CVEs that would have been treated as urgent under v3 but are now classified as Medium under v4. For security teams drowning in patches, this matters.
What This Means For Your Security Program
If You're Still On CVSS v3
You're not alone. V3 remains the dominant standard. But start preparing now by:
Understanding the gap. Look at CVEs with both scores in your environment. See where the differences are biggest. You'll quickly identify vulnerability types where v3 may be inflating urgency.
Testing in parallel. Run v4 scores alongside v3 for a quarter. Get comfortable with how the scoring differences affect your prioritization.
Updating your policies. If your SLAs are tied to CVSS scores (e.g., "patch all Criticals within 48 hours"), you'll need to adjust. A vulnerability that's Critical in v3 but Medium in v4 might not need that 48-hour response.
If You're Adopting CVSS v4
The data shows this transition is manageable. The 84.7% overlap between v3 and v4 scores means you can compare directly for most vulnerabilities.
Start with high-volume vulnerability types. SQL injection and RCE vulnerabilities show the biggest scoring differences. Focus your v4 adoption on these categories first.
Keep v3 as your baseline for now. For existing vulnerabilities already scored in v3, maintain those scores until you have a clear v4 equivalent.
Leverage environmental metrics. CVSS v4's Threat and Supplemental metrics give you better context. A vulnerability with a lower v4 base score might still be critical in your specific environment
The Bigger Picture: Severity Isn't Risk
Here's something the data makes crystal clear: Lower scores don't automatically mean lower risk.
CVSS measures severity, not risk. It tells you how bad a vulnerability could be if exploited, not how likely it is to be exploited in your environment or what impact it would have on your specific business.
That Pre-Auth SQL Injection that dropped from 9.8 to 7.0? It might still be your highest-priority item if it's in your customer-facing application that handles payment data.
CVSS v4 gives you a more accurate starting point. Better base data for your prioritization framework. But you still need to layer in asset criticality, exposure, threat intelligence, and compensating controls.
This is the foundation of Continuous Threat Exposure Management (CTEM): understanding not just what vulnerabilities exist, but which exposures actually threaten your business.
The scoring methodology has evolved, and your vulnerability management approach should evolve with it.
If you want to see how, at Hackuity, we fully support CVSS v4 and fuel it into our risk scoring algorithm to overcome the limitations of severity-based prioritization, request a short demo below, and we'll walk you through it.👇



