Navigating the Cisco Vulnerability Management (formerly Kenna) End of Life: A Strategic Inflection Point for Security Programs


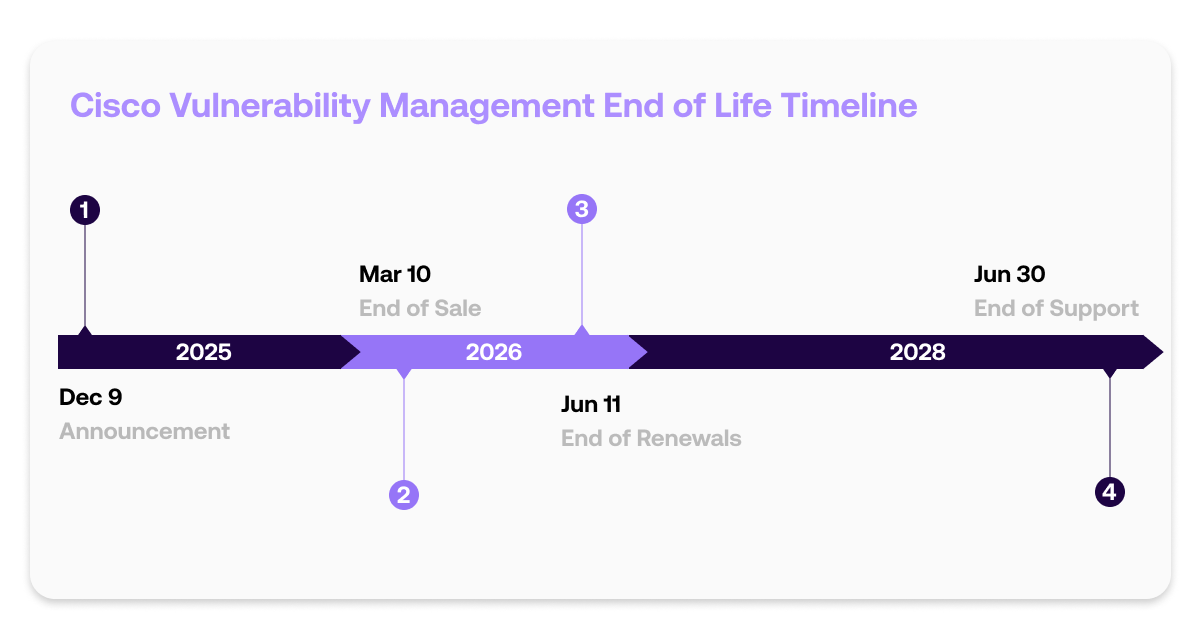
On December 9, 2025, Cisco issued an official end-of-life announcement that changes the landscape for many security teams: Cisco Vulnerability Management, Vulnerability Intelligence, and Application Security Module (formerly Kenna) will reach end-of-support on June 30, 2028.
The announcement includes a critical detail that elevates this from a routine technology refresh to a strategic decision point: Cisco has explicitly stated there is no replacement available for these products at this time. This is not a migration to a next-generation Cisco platform. It is a complete exit from this market segment, requiring customers to reassess their vulnerability management approach.The timeline provides approximately 42 months from announcement to final support cutoff.
Sales end March 10, 2026. Service renewals stop June 11, 2026. After mid-2028, organizations still running Cisco Vulnerability Management will operate without vendor support, security updates, or technical assistance.
💡Here is the good news: if your organization has been running Kenna successfully, you already have something more valuable than any platform—you have the operational foundation in place to transition smoothly and evolve further.
What Kenna Customers Already Have Right
Organizations that implemented Cisco Vulnerability Management (Kenna) did more than deploy a tool. They built an operational capability: risk-based prioritization methodologies, remediation workflows connecting security and IT teams, clearly identified asset owners and SLAs, and reporting frameworks that communicate vulnerability risk to boards and executives.
This operational maturity is what makes vulnerability management programs effective. Kenna provided the platform, but your teams built the processes, governance structures, and cross-functional collaboration that actually reduce risk.
The transition ahead is not about rebuilding this foundation. It is about preserving these capabilities while adding new ones that address the evolving complexity of modern attack surfaces.
Beyond Buzzwords: Why "How" Matters More Than "What"
The vulnerability management industry regularly cycles through conceptual frameworks: Risk-Based Vulnerability Management (RBVM), Exposure Management, Vulnerability Prioritization Technology (VPT), Continuous Threat Exposure Management (CTEM). Each promises a new approach and is often positioned against the others.
Here is the reality: These frameworks describe similar objectives: understanding vulnerabilities in business context, prioritizing by actual risk, focusing remediation where it matters most, and measuring outcomes rather than activity. They are not in opposition, but reflect a shared goal: moving beyond reactive patching toward strategic risk reduction.
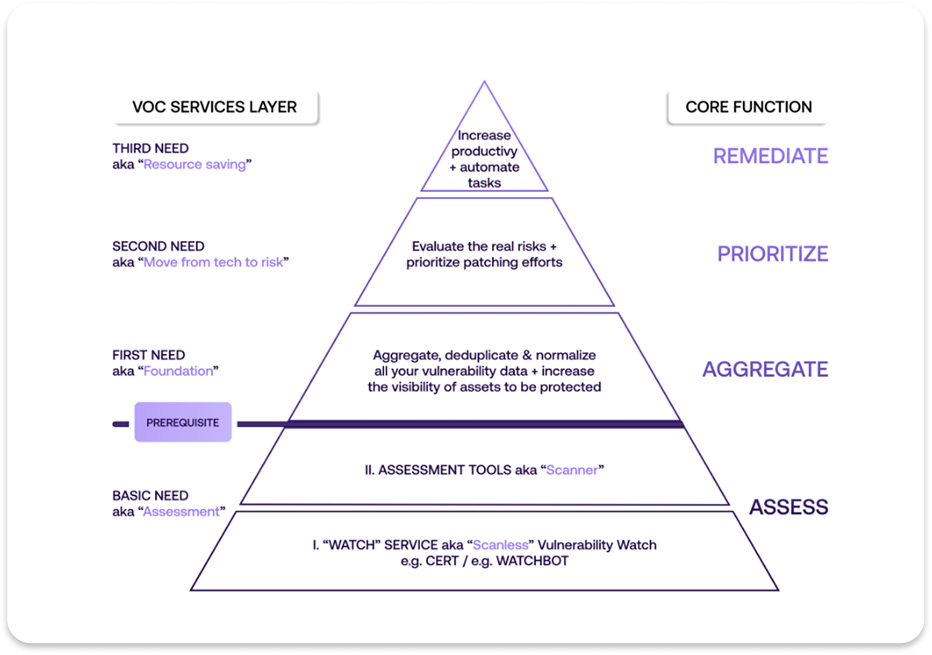
What truly differentiates security programs is not which framework they adopt, but how they implement it. This is where the Vulnerability Operations Center (VOC) model comes in. Not as another concept, but as a concrete organizational approach combining people, processes, and technologies to operationalize risk-based vulnerability management.
A VOC is the preventive counterpart to a SOC (Security Operations Center). Where SOCs focus on logs, indicators of compromise, and incidents, VOCs focus on assets, vulnerability findings, and remediation orchestration. Where SOCs respond to threats, VOCs anticipate them through systematic attack surface and risk reduction.
A VOC does not replace RBVM or Exposure Management: it is how those concepts are implemented at scale. Organizations that have run Kenna successfully have already built many of the VOC capabilities that matter most.
The Real Transition Challenge: Continuity Plus Evolution
For organizations transitioning from Cisco Vulnerability Management, the challenge is straightforward: maintain operational continuity while extending capabilities where gaps exist.
- What you need to preserve: integration architectures linking VM to ticketing, CMDB and orchestration tools, established workflows and SLA frameworks, and the institutional knowledge built around risk-based prioritization.
- What you should add: extended coverage across cloud, container, OT, identity, application security domains and penetration-testing, be them CVE or misconfigurations, modern standards such as CVSS v4, enhanced deduplication capabilities to automatically merge assets and identify inefficient overlaps between your scanners.
Vendors presenting this transition as a complete rethinking of vulnerability management are overcomplicating it. Your goal is not to start from scratch, but to extend an existing, mature operational model beyond the technological limits Kenna has reached.
Why the Migration Can Be Simpler Than You Think
At Hackuity, we work extensively with Fortune 500 organizations building and maturing vulnerability operations programs. Our experience confirms what successful security leaders already know: the best technology cannot compensate for unclear responsibilities, undefined processes, or misaligned objectives.
Process and strategy come first. Technology enables.
This is good news for Kenna customers. The hard work, defining processes, stakeholders, governance frameworks, and operational discipline, has already been done. You are not starting a vulnerability management program; you are migrating an existing and functioning one.
What Hackuity Adds to Your Existing VOC Foundation
As a recognized leader and the only European pure player in the Forrester Unified Vulnerability Management landscape (Q1 2025), Hackuity helps organizations elevate their VM maturity through focused strengthsI
ts laser-focused R&D dedicated entirely to vulnerability management maturity, informed by real-world Fortune 500 use cases, continuously improves operational effectiveness.
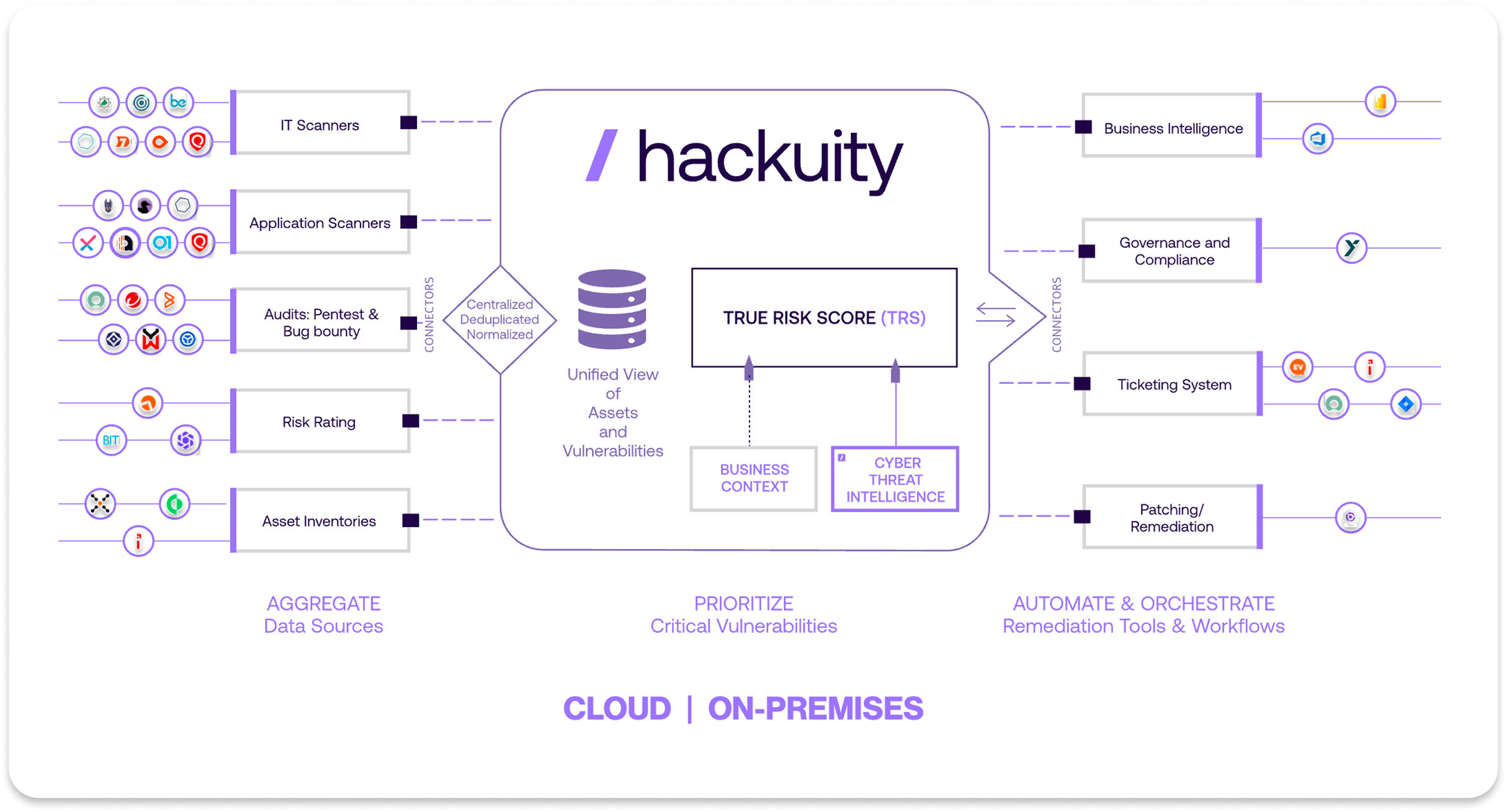
Hackuity’s true vendor agnosticism, with 100+ native integrations, ensures consistent normalization and deduplication across your entire attack surface. We do not sell scanners, do not inject proprietary data, and treat all sources equally, unlike platforms that favor their own tools. This neutrality is critical in heterogeneous environments with multiple scanning technologies.
Hackuity’s transparent and tunable prioritization is built on an award-winning risk algorithm that is fully transparent. No black boxes or opaque scoring. You can see all inputs, understand the methodology, and adjust parameters to match your organizational context, ensuring trust and control. In an industry dominated by opaque proprietary and AI scoring systems, transparency is operational, not philosophical.
Advanced data normalization, including the 2024 asset correlation engine v2.0, delivers tangible operational impact at scale. Flexible deployment options, SaaS or on-premise, accommodate regulatory compliance and architectural constraints.

Your Migration Path: Practical Steps
For Kenna customers ready to evaluate alternatives, the migration process is straightforward:
🟢 Weeks 1-2: Assessment & integration mapping
Inventory existing integrations, workflows, and reporting needs; map asset and vulnerability data to migrate; identify stakeholder reporting formats to retain.
🟡 Weeks 3-4: Parallel deployment & validation
Deploy Hackuity alongside Cisco Vulnerability Management, replicate key integrations, and validate improved data normalization and deduplication.
🟠Weeks 5-6: Workflow transition & team training
Migrate remediation workflows to Hackuity, train analysts on expanded capabilities, and run parallel reporting to ensure continuity.
🔴Weeks 7-8: Cutover & optimization
Finalize the transition to Hackuity as the primary platform, decommission Cisco Vulnerability Management, and start enjoying the increased operational efficiency and clarity around Risk with the improved capabilities.
This timeline assumes mature processes and well-defined requirements, typical of Kenna customers.
Moving Forward: Continuity Without Compromise
The Cisco Vulnerability Management end-of-life creates forced change, but it does not require starting over. Organizations running Kenna successfully have already solved the hardest problems: governance, cross-functional workflows, metrics, and organizational buy-in.
For Kenna customers evaluating their path forward, Hackuity offers seamless migration support, free migration services, a platform designed for VOC operational maturity, and capabilities that extend beyond Kenna’s limitations while preserving foundations that already work.
The path forward does not require reimagining your vulnerability management program. It requires a platform partner that understands the operational maturity you have achieved and can help you build on it.
If you are beginning to plan your transition from Cisco Vulnerability Management, let’s discuss how Hackuity can support continuity while adding the capabilities your program needs next. 👇



