From Risk to Decisions: Why SSVC Is the Missing Piece


You've got better severity scores. You've got risk context. Now you need to actually decide what to do.
This is the final piece of the puzzle. In our first article, we covered how CVSS v4 improved severity measurement. In the second, we explored how TRS adds threat and environmental context to calculate actual risk. But even with accurate severity and comprehensive risk scoring, most vulnerability management programs stall at the same point: turning data into consistent decisions.
Your team knows which vulnerabilities are risky. But how do you consistently decide what gets fixed this week versus next month? How do you explain those choices when engineering teams push back?
SSVC (Stakeholder-Specific Vulnerability Categorization) solves this. It turns your risk signals into defensible, repeatable decisions.
The Decision Problem
Your team looks at a TRS 850 Finding. Is that "fix now" or "schedule for next sprint"? What about TRS 780? Where's the line? Different team members draw it differently.
Or you set a simple rule: "Fix all Critical and High." Sounds clear until you realize you have 200 High Findings and two engineers.
SSVC replaces arbitrary score thresholds with customizable decision trees.
What SSVC Does
SSVC was created by CISA, with contributions from CERT/SEI at Carnegie Mellon University. It categorizes vulnerabilities into action-oriented remediation pools based on your organization's specific context.
Unlike CVSS, which gives you a severity score, SSVC gives you a decision. It uses decision trees tailored to three factors:
Your handling capacity - How many people can you mobilize to fix vulnerabilities?
Your risk appetite - How much risk can your organization tolerate?
Your applicable regulations - What compliance frameworks mandate specific security levels?
The output: four remediation pools with clear timelines.
The Four Remediation Pools
💣 IMMEDIATE - Highly dangerous vulnerabilities requiring immediate action. Ticketed daily, target date: current date plus 3 days.TRS captures how your infrastructure and security posture affect risk:
⏱ OUT OF CYCLE - Critical vulnerabilities addressed before the next scheduled patching period. Ticketed weekly, 15-day target.
📅 SCHEDULED - Vulnerabilities addressed during planned patch cycles. Ticketed bi-annually aligned with maintenance windows.
🗑 DEFERRED - Least critical vulnerabilities temporarily deferred. Monitored via queries, no immediate tickets.This structure aligns with how remediation actually works: emergency fixes, urgent patches, scheduled maintenance, and backlog.
How the Decision Tree Works
You build a decision tree based on factors that matter to your organization:
Exploitation status - Is this actively exploited? Is exploit code available?
Technical impact - What happens if exploitation succeeds?
Mission impact - How does this affect business operations?
System exposure - What controls exist? Is it internet-facing or internal?
You define the logic once: "If exploitation is active AND exposure is internet-facing AND mission impact is high, then IMMEDIATE." The system applies that logic consistently.
Why This Beats Score Cutoffs
Score-based prioritization is context-blind. A Critical vulnerability on an air-gapped dev system doesn't need the same urgency as one on your customer-facing API. Score cutoffs can't capture that nuance.
SSVC makes the reasoning explicit. A vulnerability lands in IMMEDIATE because it meets multiple conditions simultaneously. You can explain that logic to anyone.
Different parts of your organization can use different decision trees while maintaining consistent methodology. Your internet-facing production systems might use an aggressive tree. Your internal development systems might prioritize scheduled remediation. SSVC formalizes those differences instead of handling them through informal exceptions.
Implementing SSVC in Hackuity
Here's how we make SSVC operational:
1. Define Your Decision Tree
Your SSVC logic depends on your organization's remediation capacity and risk appetite. A small team with limited resources needs a different tree than a large security organization.
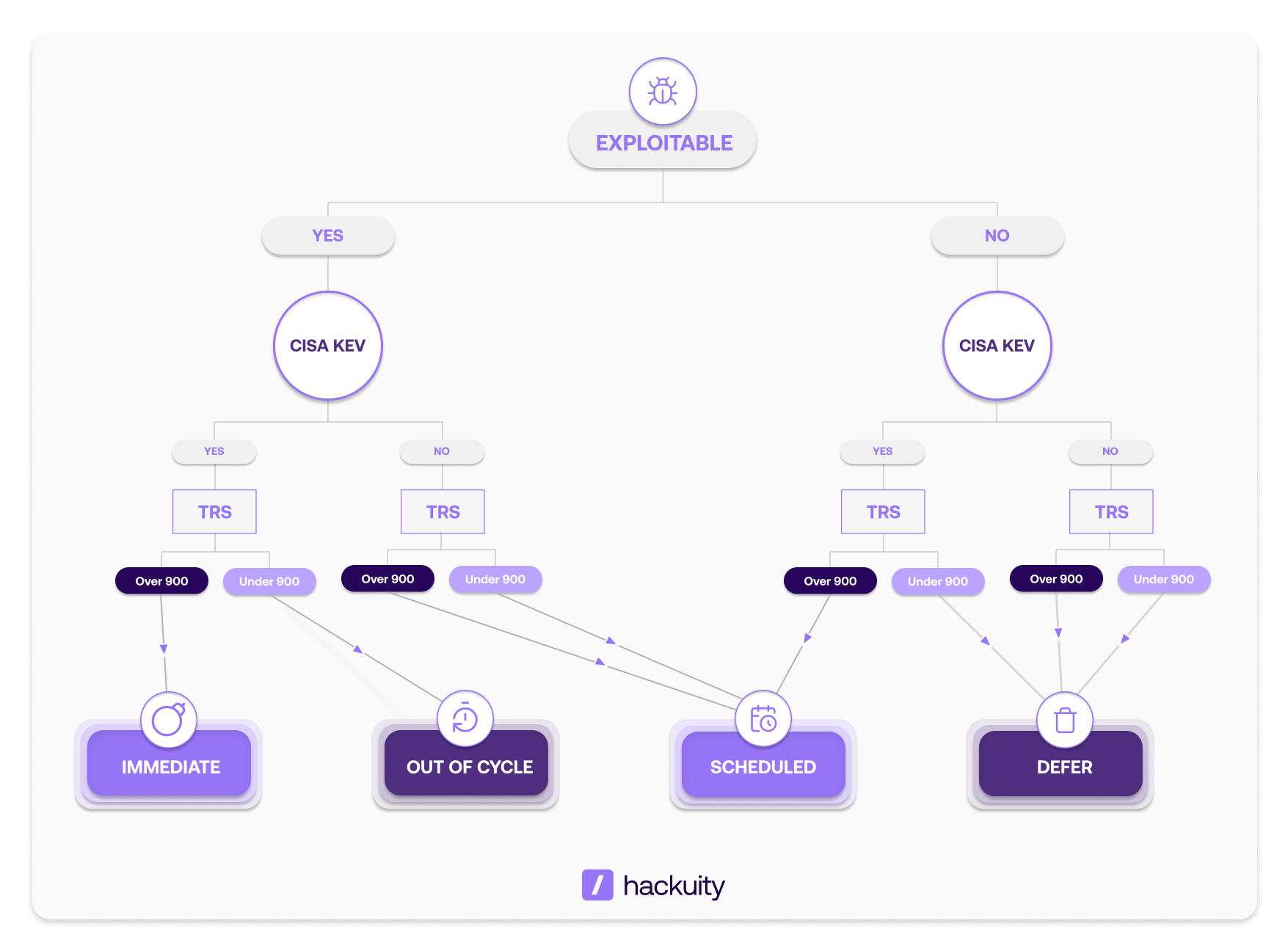
Example for an organization with very limited remediation capabilities
The tree structure you build determines how findings flow into your four remediation pools. Organizations with high capacity can route more vulnerabilities to IMMEDIATE and OUT OF CYCLE. Smaller teams need conservative trees that prioritize only the most critical combinations into urgent pools.
2. Automate Pool Assignment
Once your decision tree is defined, every new Finding gets evaluated automatically. In Hackuity, you do this with Remediation Groups. Each Remediation Group uses an advanced query that captures all the decision tree branches leading to that pool. Findings matching the criteria automatically join the appropriate group: IMMEDIATE, OUT OF CYCLE, SCHEDULED, or DEFERRED.
.png)
Example query capturing SCHEDULED pool criteria
As vulnerabilities arrive and threat intelligence updates, Findings move between pools automatically. A vulnerability that starts in SCHEDULED can jump to IMMEDIATE if exploit code appears or threat intensity spikes.
3. Automate Ticketing to Operational Teams
With Findings automatically categorized into pools, the final step is distributing work to the teams who fix them.
Hackuity creates tickets directly in your ITSM with all the context needed: vulnerability details, affected Assets and remediation guidance. Teams see exactly why this Finding matters and what action to take.
For larger organizations, you can create separate Remediation Groups by team or technology stack. Your Windows team gets their IMMEDIATE Findings in their board. Your cloud team gets theirs. Same SSVC logic, targeted execution.
The ticketing cadence follows your pool definitions: daily for IMMEDIATE, weekly for OUT OF CYCLE, aligned with patch windows for SCHEDULED.
Why It Matters
SSVC reduces friction. Less time debating which vulnerabilities to fix means more vulnerabilities get fixed.
CVSS v4 gave you better severity measurement. TRS gave you comprehensive risk context. SSVC gives you the operational framework to act on both, consistently and at scale.
If you want to see how to build an SSVC tree that fits your organization and integrate it into your workflow, request a demo below. We'll walk you through a working session tailored to your environment. 👇



